|
Download
Swat It
Completely
FREE program that scans your files for Trojans, Worms, Bots
and other Hacker programs
A trojan is like
having remote control over a computer. Many kiddy scripts out
there have trojans hid inside them unbeknownst to the
bully using them they have fallen prey. Poetic justice in a
way. Other kiddy scripts implant them. Lets have
an in-depth look at a trojan so you can see the implications
this has.
Sub 7 was created by
mobman - after fooling around with netbus he simply
reversed netbus and got subten which he later changed to
subseven or so the underground rumour mill tells me
When
the server program is installed, the computer is exposed
to attacks. Once the connection is established, the
attacker can acquire sensitive information such as passwords
and it gives them total control of your computer and
they can monitor and record everything you do. That can give
hackers the power to devastate you once they have gathered
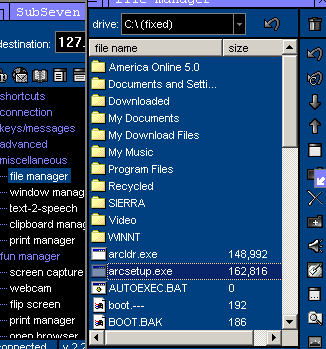
enough information. I have a couple screen shots of sub 7 for
you here as well as what comes with it.

Main Distributed Package:
Arrives in a zip file called Sub717.zip containing
- server.exe - Server (325k)
- Sub7.exe - Client (458k)
- EditServer - Server
configurator (182k)
+ a readme.txt file.
Name: Sub 7
Version: Current Version 1.7
File Sizes: See Above
Affected Operating Systems: Win95 & 98 - NT???
Listen ports (default): 1243, 6711, 6776 TCP
Startup Routine: Registry
Written in: Unknown
Severity: Medium/high Risk
SETUP SERVER. you can setup
the server before sending
it to the victim.
PACK the server.exe with another EXE file or
with an image.
Change the victim's resolution.
E-mail notify.
See all the running processess [visible or not]
Print feature! allows you to specify a text to be printed on
the victim's printer
Registry editor.
Find files feature.
ScrollLock, CapsLock, NumLock can be turned ON and OFF
Disconnect victim. hangs up the victim's connection to the net
Focus window
Screen Preview (screen dump)
ICQ notification
Show image feature.
Continuous screen capture is finally here!
Flip screen.
Hide/show the victim's desktop icons.
FTP server.
Message manager.
Enable or disable Ctrl-Alt-Del.
Send keys.
Open the default browser at the specified address
Hide or show the Start button
Disable keyboard
Chat with the victim.
Start/stop the victim's PC Speaker.
Restart windows.
Open/close the CD-ROM
Set the length of the victim's mouse trails.
Get all the active windows on the victim's
computer. after that you can:
- close a specified window
- enable/disable a specified window
[the victim will or will not be
able to interact with it]
- disable the close button on a specified window
- hide or show a specified window
Get a list of all the available drives
on the victim's computer
Turn monitor on/off.
Show/hide the taskbar.
Get system information like: windows version,
user name, company name, screen resolution, etc.
Keylogging
Record Audio.
File manager.
Reverse/restore mouse buttons.
Get passwords.
Offline key logger.
Trojans can hide in just about anything
and can look like truly legit progs, sub
seven in particular because it is so small.
At first it was thought to be a minor pain
but has proven to be a giant kick in the
head with a golf shoe
To protect yourself please read the
ip addy section, firewall section and my
security column entiled "feeling lucky punk?"
to learn how to maximize, test and expand your
port hiding skills.
If you would like to get revenge on a lamer
who sent you sub seven, run EditServer.exe
and open up the Sub7 server file. If it's not
you can view their ICQ UIN or email address.
'PING their ip to find there IP's hostname,
real name and phone number and mailing adress
if you go about it right. Notify their ISP.
Download NetSpyHunter
*FREE* NetSpyHunter monitors ports and scans your registry/hard drive for trojan activity. It prompts you with a message box and sound when an intruder is detected. It also scans Windows registry/hard drive for trojans. It features an automatic listen mode at start-up
|